First published on MSDN on Mar 24, 2018
I worked on a new situation, when we need to connect to a Azure SQL Database using SQL Alias in the same way that we have SQL Server on-premise. Unfortunately, there is not supported , but we are going to test and make it successfully.
As the alias is not supported in Azure SQL Database let me share with you 3 alternatives:
ALTERNATIVE 1: Using SQL SERVER Management Studio and cliconfg 64 bits - “C:\windows\syswow64\cliconfg.exe”
ALTERNATIVE 2: Using SQL SERVER Management Studio and modify the C:\Windows\System32\drivers\etc\host
ALTERNATIVE 3: Using SQL SERVER Management Studio and cliconfg 32 bits - “C:\windows\system32\cliconfg.exe”
Enjoy!
I worked on a new situation, when we need to connect to a Azure SQL Database using SQL Alias in the same way that we have SQL Server on-premise. Unfortunately, there is not supported , but we are going to test and make it successfully.
As the alias is not supported in Azure SQL Database let me share with you 3 alternatives:
ALTERNATIVE 1: Using SQL SERVER Management Studio and cliconfg 64 bits - “C:\windows\syswow64\cliconfg.exe”
- First, lets try to open the cliconfg for 64 bits, we provided the name of the alias, our server name and TCP/IP protocol.

- Second, we are going to connect to our Azure SQL Database using the alias name.

- Third, I need to specify in the user name username@servername, because working with Azure SQL Database, all connections will go through a Proxy/Firewall, (you don’t have a physical server you have a logical entity). This firewall/proxy receive the incoming connection and reroute the connection to the server that is running your database (each database that we have in Azure is running in different virtual machines, except, elastic pool that are running multiple databases in the same SQL Instance and hence in same virtual machine)
ALTERNATIVE 2: Using SQL SERVER Management Studio and modify the C:\Windows\System32\drivers\etc\host
- First, I identified the current IP for proxy/firewall for the server (unfortunately, this IP could change without notice and we cannot provide these IPs for this proxy/firewall but normally it might not change too often.
- Change the file C:\Windows\System32\drivers\etc\host adding a new entry.
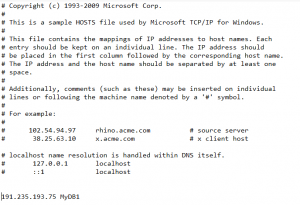
- Using SQL Server Management Studio, connect to the server, like this:

ALTERNATIVE 3: Using SQL SERVER Management Studio and cliconfg 32 bits - “C:\windows\system32\cliconfg.exe”
- Unfortunately, I don’t have any operating system in 32 bits, but, following the details of Alternative 1 it should be work.
Enjoy!
Updated Mar 14, 2019
Version 2.0Jose_Manuel_Jurado Microsoft
Microsoft
 Microsoft
MicrosoftJoined November 29, 2018
Azure Database Support Blog
Follow this blog board to get notified when there's new activity